Technical Details
- Activation explained
- Online license management server
- Typical use of activation
- Advanced license management
- Registration services supported
- Product keys and Executable Protection
See also
Activation Explained
License enforcement using the product activation technique ensures that each license product is used in compliance with its licensing terms. When installed on a new PC, a product starts the Activation Wizard that (with the user's permission) queries a centralized license server via the Internet, asking for permission to run. The license server then either grants or denies permission according to the software licenses owned by the end-user. In case a permission is granted, the product receives a unique Activation Code that can be used to verify the product's activation status; a positive result will only be returned if the activation code is used on the very same PC it is obtained for.
The user will have a 14-day (or a different period defined by the end user license agreement) grace period when the product will display an activation reminder. After the end of the grace period only the activation reminder functionality will work in the product.
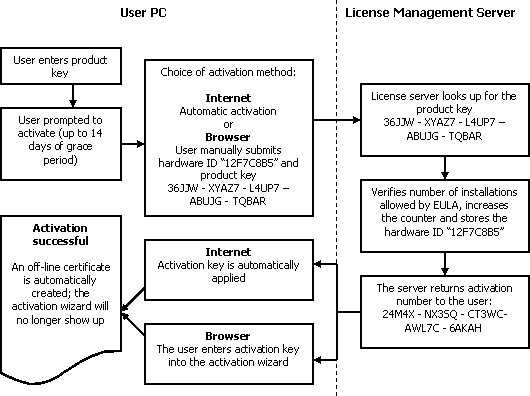
Online License Management Server
As a developer, you will get access to the license management server. The server stores all your customer's product keys in one place, allowing an automatic key reminders to the users.
The server also allows you to manage registration and activation keys, block a particular registration key (effective immediately) or unblock ones that were blocked by excessive number of failed activations. You can change the activation policy in effect at any time, relaxing or strengthening current activation policy. The server provides you with a valuable statistics on your products use.
It is easy to start and to stop using our service: we will provide you with tools that will allow you to generate your registration and activation keys locally on your PC or on your own Internet server.
Activation Policies
There are several pre-defined policies the developer can use to manage licenses. This is a per-product setting.
- Monitor only mode. In this mode the system will not block any activation requests. It will simply log the requests and record the statistics.
- Massive fraud prevention only. This mode will only refuse to give the activation code after a fair amount (what is "fair" is yet to be defined) of activations is made from different computers. Such registration number will then be marked as stolen and invalid.
- License terms enforcement – fair use. In this mode a system would only allow a fair number of complimentary activations per purchased copy. A "fair" use for a general purpose program would be single additional activation per copy (say, business & home, or stationary & laptop computers).
- Strict license terms enforcement. For expensive products strict license enforcement may be required. An activation code will be issued for a single PC only; re-activation will succeed on the same PC (for a "fair" number of times – say, up to ten per month) but fail on a different one.
For advanced users
It is possible to create different methods…
- Trial or evaluation period. Will allow using the program for a pre-defined number of days (executions), after which will require activation. Useful for free- or shareware programs.
- Software rental. Will require on-line re-activation every N days (number of executions). Will be useful for programs with periodical renewal.
- Temporary registration keys. The product will allow issuing temporary registration keys that will expire after a certain number of days (executions). This can be used for demo purposes.
Default policy is defined on per-product basis. If one likes to have a different activation policy, a new product shall be created
Policy Control Parameters
Each activation policy is defined by a set of the following parameters:
- Activation period: a number of days after which the activation counter is cleared (if the user has exceeded the number of allowed activations, then the license will again be available for activation).
- New activations allowed per activation period. Every time the product is activated on a new PC the counter is decreasing. If an attempt is made to activate the program on a new machine after exceeding the number of allowed activations, the activation will fail.
- Number of re-activations allowed per activation period. If an attempt is made to re-activate the program on the same machine (re-activation) after exceeding the number of allowed activations, the activation will fail.
- Fraudulent use threshold is a number of failed activation attempts after which permanent block is put on the the registration code affected.
Registration Keys
Our service will issue and manage registration keys
for the products. A typical registration key consists of 25 characters divided
by 5 groups: 4SCQH-Q6W9X-QAB4M-YB3DY-Z682C
.
The keys are generated using an asymmetric open-key crypto algorithm (that is, only you
can generate the key but everyone can verify them).
Registration Services Supported
Currently we have scripts for automatic Product Key generation and delivery for the following software registration services:
- Register Now!
- ShareIt
Executable Protection
We currently support ASProtect (http://www.aspack.com/asprotect64.html). ASProtect will encrypt the code of your application.
Registration keys contain a special security feature that allows our SDK to dynamically decrypt and encrypt vital sections of the executable file using the ASProtect (http://www.aspack.com/asprotect64.html). It can be used if ASProtect is used to protect the executable file, which is highly recommended. Technically, it works the following way:
- The fragments of code that are to be executed only in the registered version of the program are marked in the source code of the application with begin and end marks (defined in the ASProtect SDK)
- The application is compiled
- The constant from your registration key is put to the file, and ASProtect is told about the file with the constant
- The compiled application is processed with ASProtect. ASProtect looks through the application code and encrypts the marked fragments of code using the constant
For registered version:
- After the application startup and verification of the key but before executing the encrypted fragments the constant from the key is extracted ASProtect API calls the ASProtect decryption routine and passes it the constant
- The decryption routine decrypts encoded pieces and after that these pieces can be executed
For unregistered version:
- After the application startup and verification of the key you don't have the constant and so you don't pass anything via ASProtect API
- The ASProtect API decryption function does not decrypt the encrypted fragments, and on execution they are automatically bypassed (when encrypting the code ASProtect inserts jump command to bypass the encrypted fragment)
Our SDK supports ASProtect key activation.